Access to corporate network: let's get things in order with NAICE

Introduction
Corporate networks are bustling with activity every day: hundreds and thousands of devices operate via wired and wireless channels. They are joined by a continuous stream of new connections: employee workstations, wireless access points, network equipment, guest smartphones, IoT sensors, servers, etc.
In this stream, administrators must ensure maximum infrastructure security and quickly solve access problems. They should clearly distinguish “who is who” and be sure that only trusted devices are connected to important resources.
In this article, you will learn how the NAICE system helps to get things in order with access to the corporate network and make life work easier for administrators.
For all network accesses
NAICE is a single control center for wired and wireless connections in a corporate network, developed by Eltex. This is a modern access system that we are actively developing, adding new features with each new release. NAICE is a multi-vendor system compatible with equipment from various manufacturers. It combines the tools:
- for authentication and authorization of users and devices;
- of their checking for compliance with security policies;
- of dynamic assignment of connection rights to network resources;
- of managing administrator access to network equipment.
A single interface for managing all connections
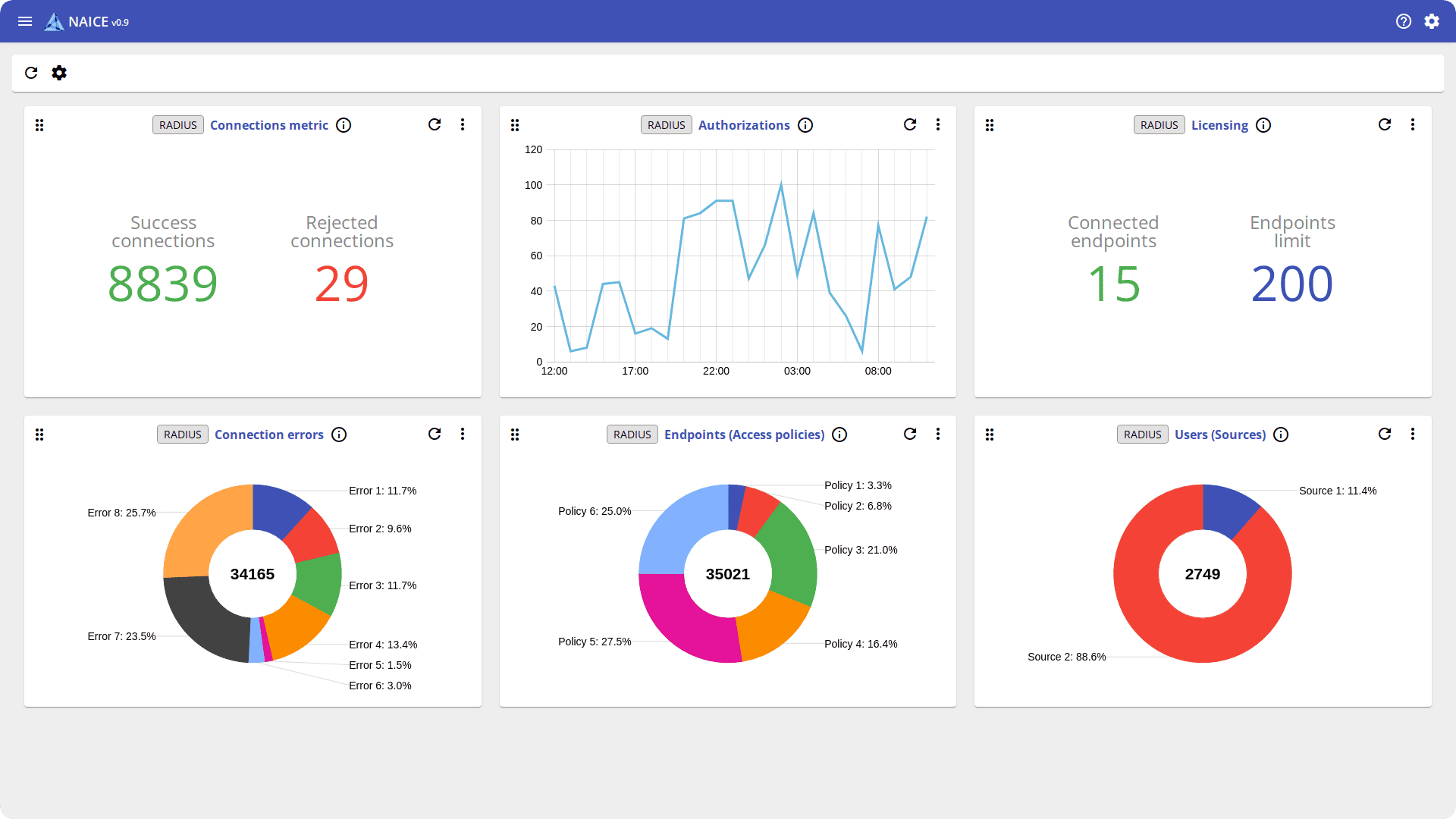
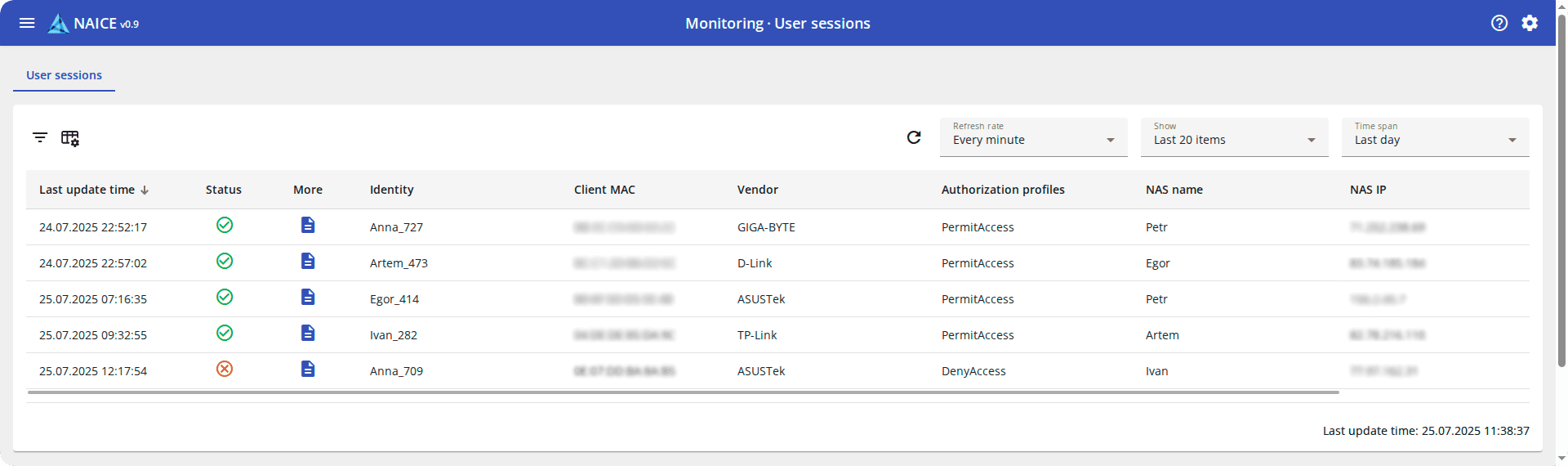
Centralized monitoring via a web interface provides administrators with a complete picture of network connections in real time. It has everything that is needed to track network connections: what is happening at the moment and where problems may occur.
At the same time, NAICE can flexibly manage connections. Administrators can configure detailed policies and different registration scenarios for each user group or device type.
Base for AAA
We have laid in NAICE a solid foundation of proven tools and industry standards.
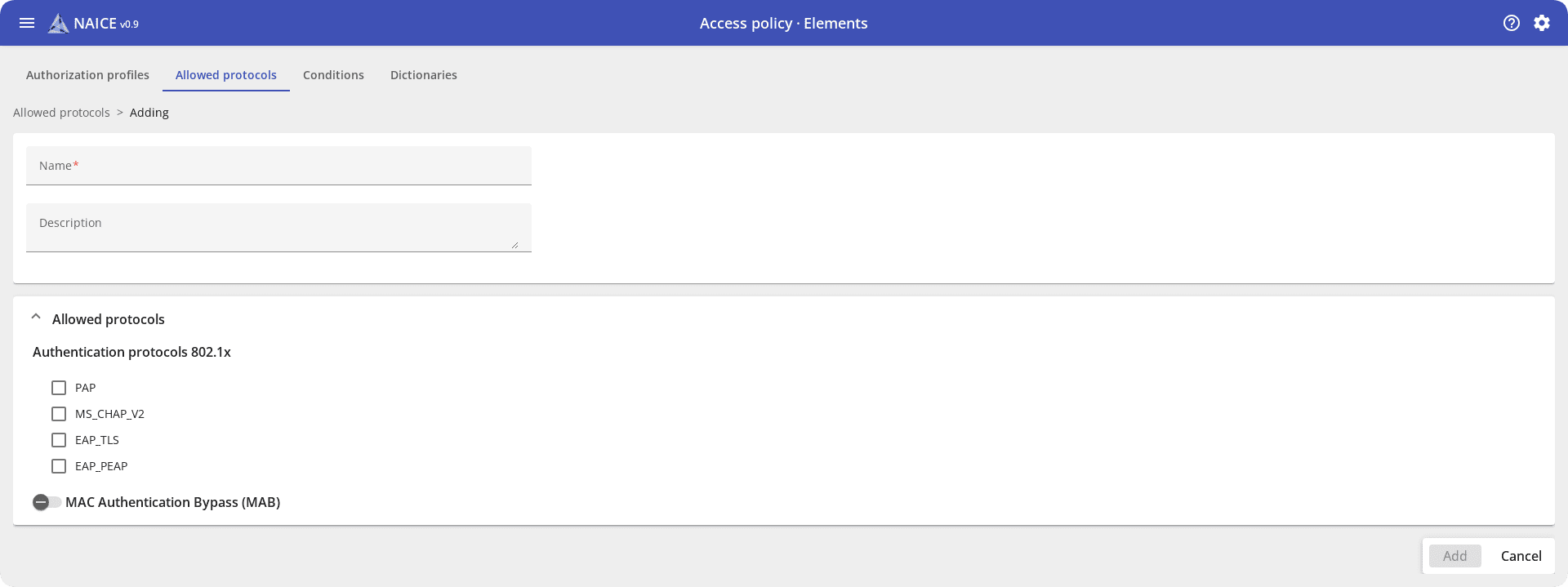
It is based on the 802.1x (RADIUS) authentication, authorization, and accounting protocol (AAA) with support for EAP-PEAP, PAP, and MSCHAPv2 methods. Authorization can also be based on MAC addresses (MAB) for devices that do not support 802.1x, and EAP-TLS using digital certificates integrated through the MS CA certification center.
Data sources
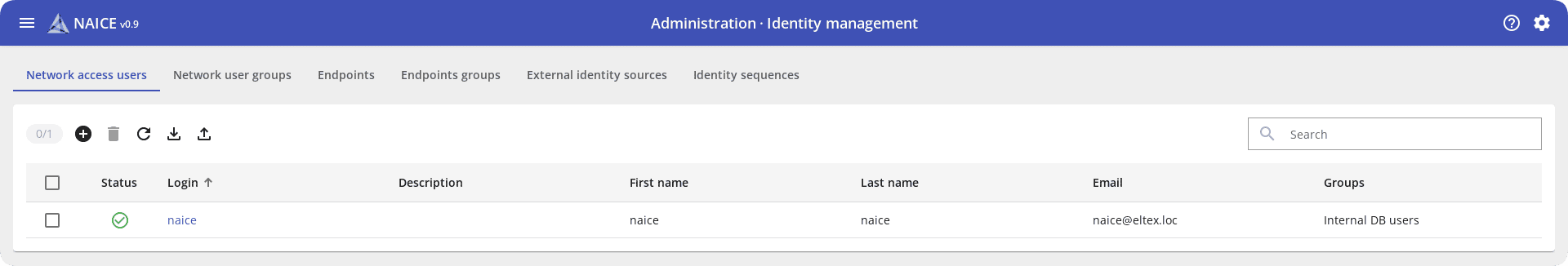
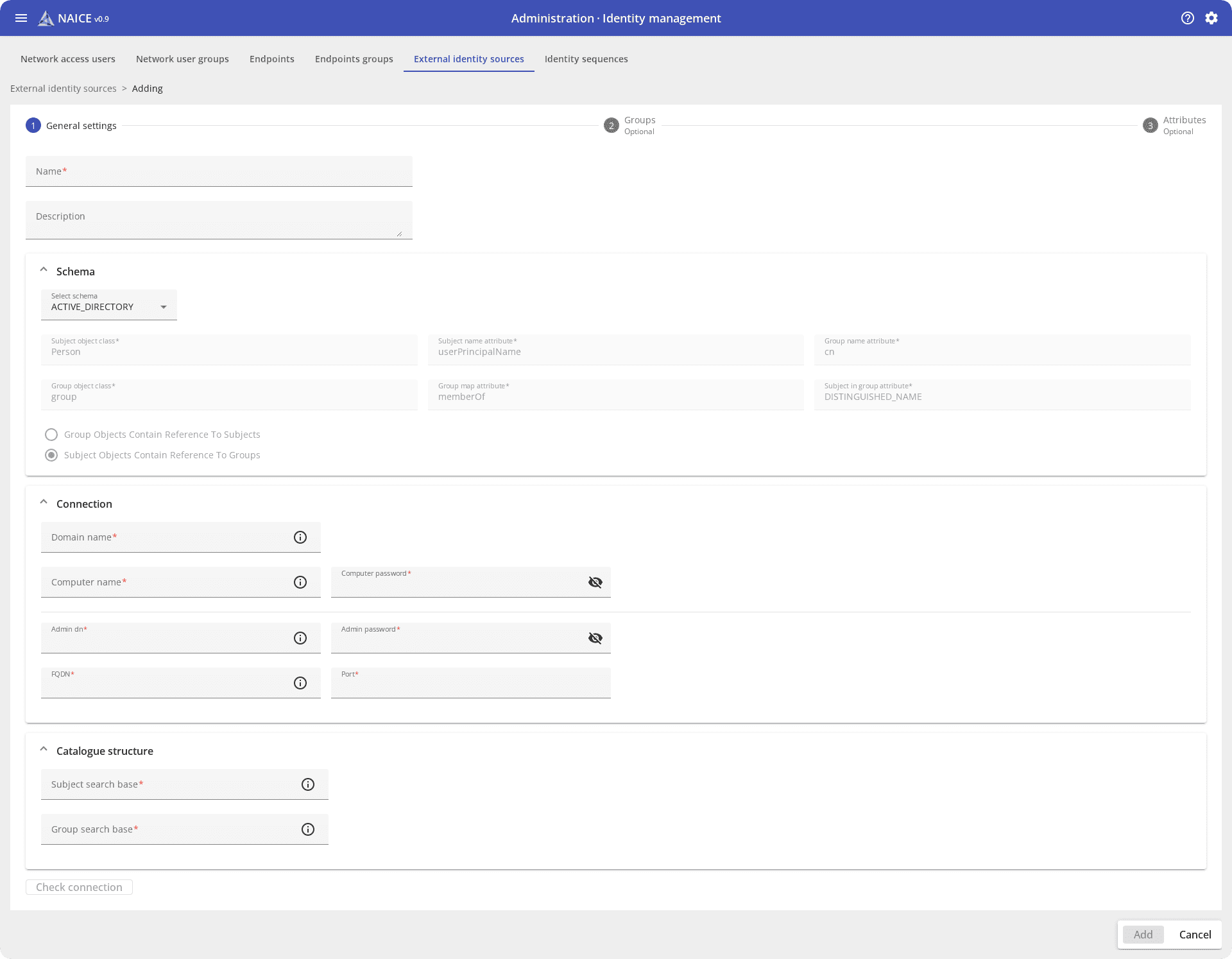
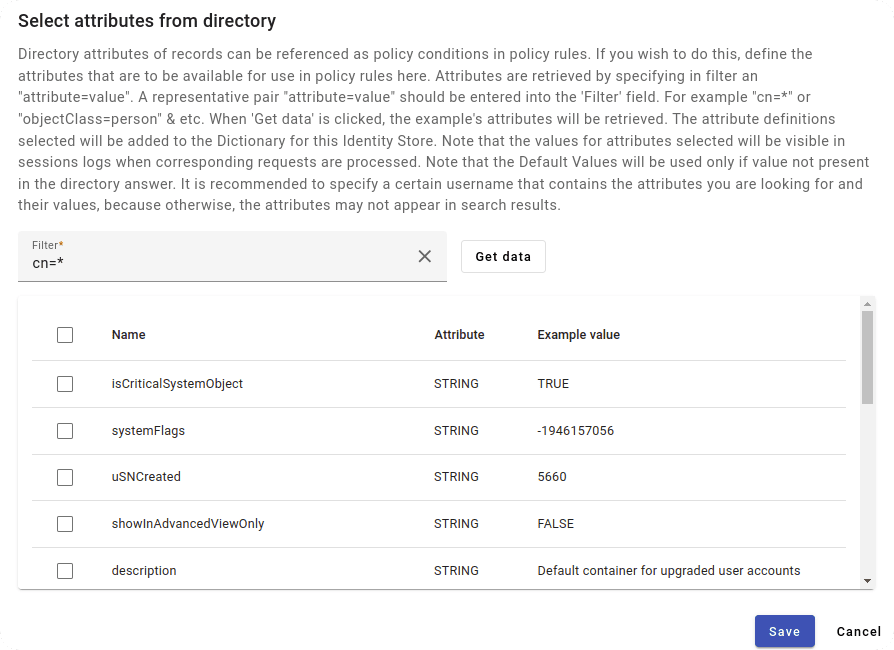
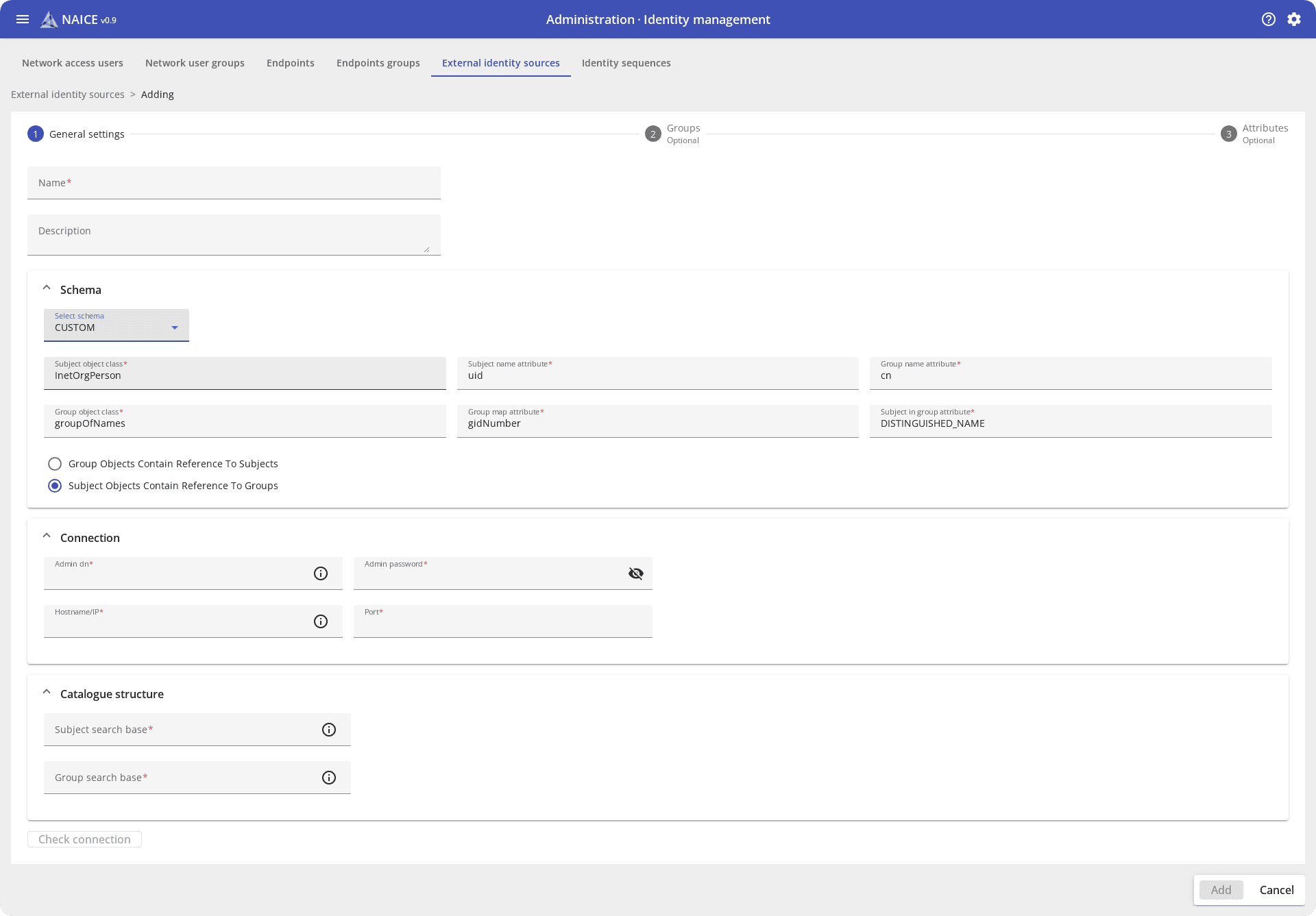
In addition to the local user database, NAICE interacts with external identification sources such as MS Active Directory and OpenLDAP. This allows using existing corporate databases for access control without having to duplicate accounts: the system works directly with corporate directories.
The user logs into the network in the usual way: through corporate accounts. NAICE receives information about their access rights from an external source and applies the appropriate access policies. This is important for large organizations, where there may be thousands of accounts.
Employees can move between departments, change positions or quit. With NAICE the administrator does not have to remember these changes and change the data in the access control system: everything happens automatically based on AD data.
TACACS+: control down to the command level
User access is half the battle. It is equally important to control the actions of those who manage critical infrastructure. For this purpose, NAICE has a TACACS+ server of Eltex own design, which provides authentication and authorization of network equipment administrators.
The system logs administrator actions, flexibly differentiates rights and available command lists on the equipment. For example, one administrator can only execute monitoring commands, another can configure interfaces, and a third has full rights.
Each equipment control command is saved in a log with a link to a specific administrator. If problems arise, you can track exactly on each device by whom, when, and what was done.
Network access for guest users
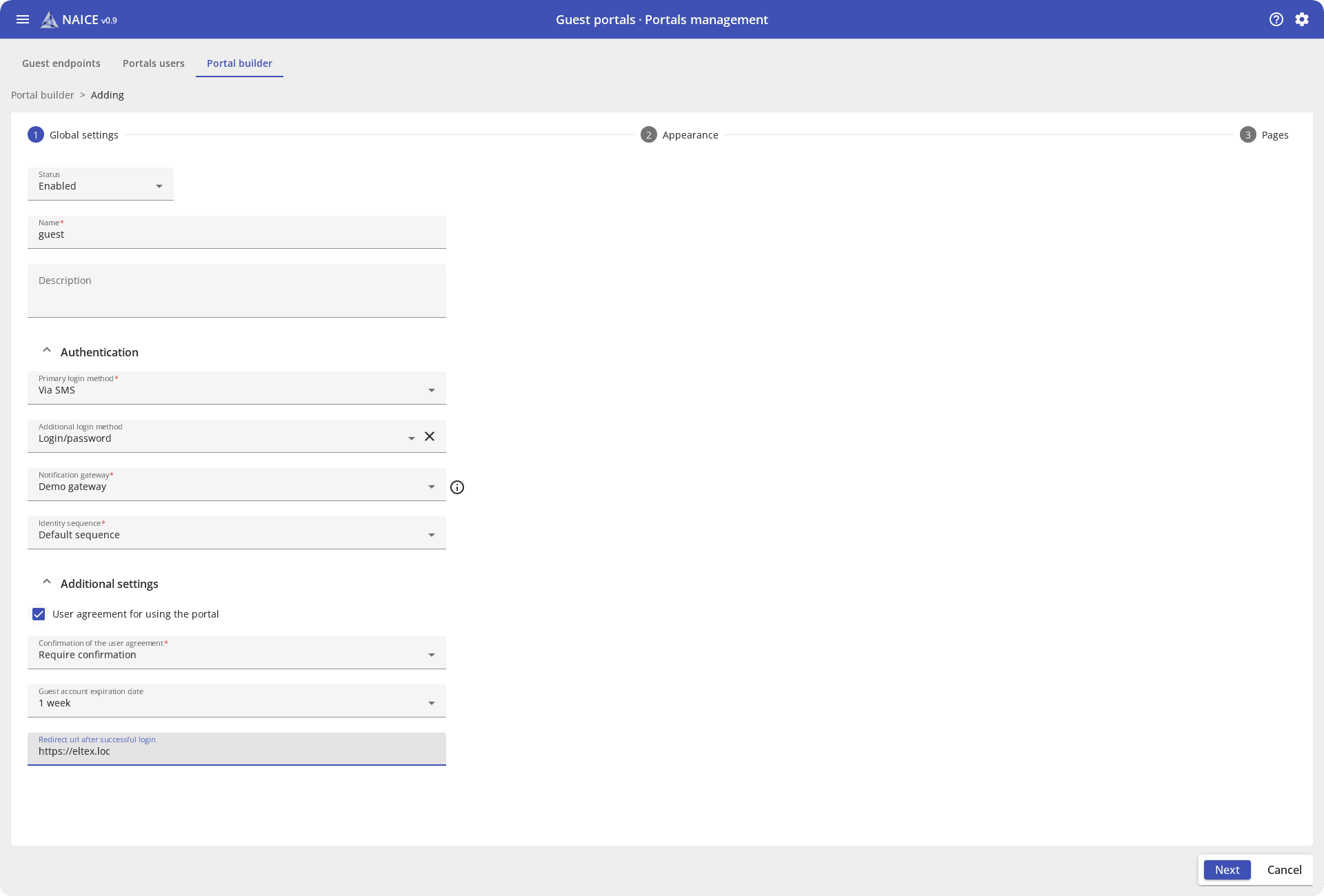
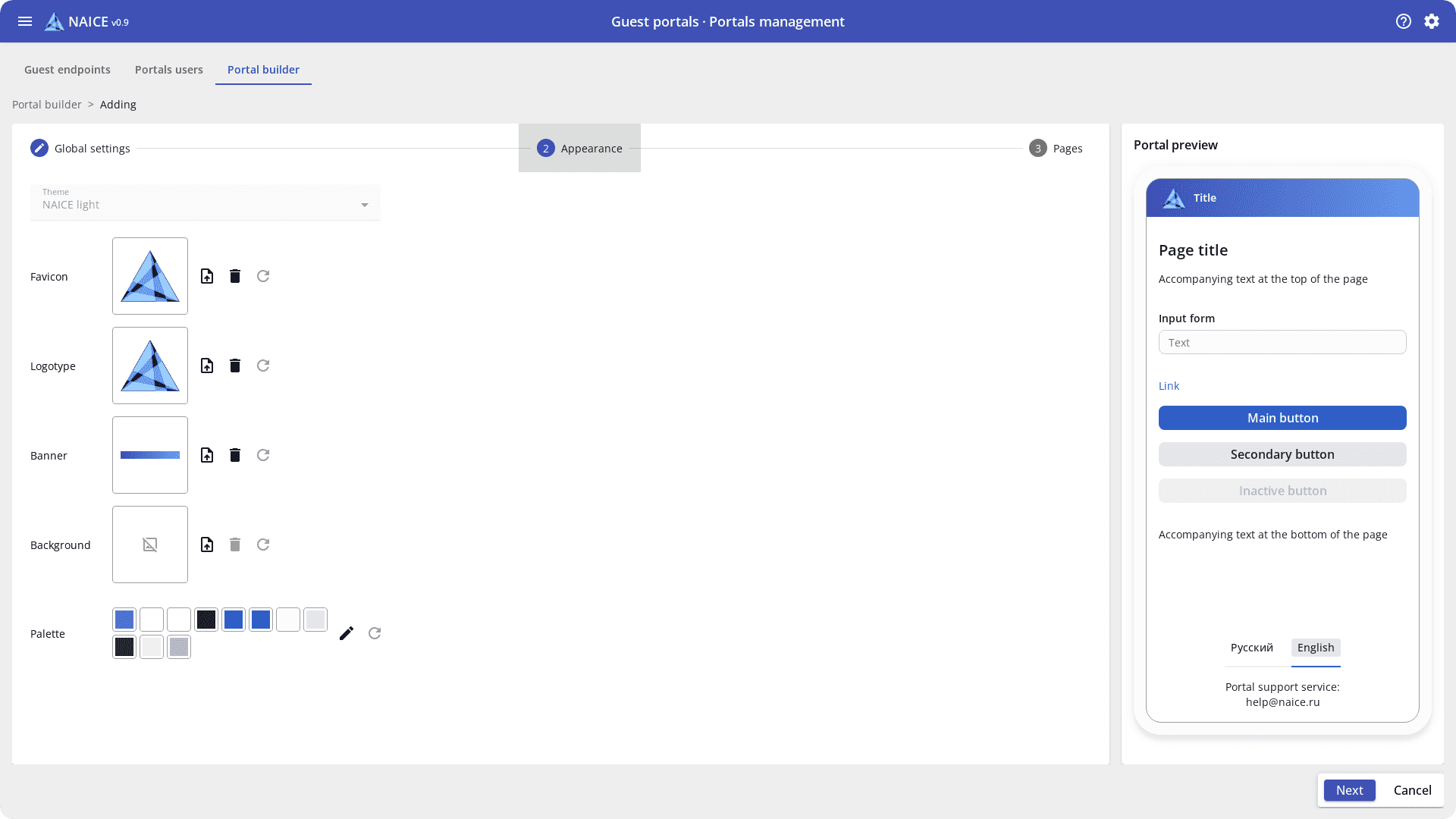
How to provide temporary Internet access to company guests? Starting with version 0.9, NAICE has a guest portal (Captive Portal) with authorization via SMS, LDAP, AD, and an internal database.
Once a user connects to the guest Wi-Fi network, NAICE redirects them to the authorization page. The phone number is entered, and the user receives an SMS with a code and logs into the network. Users get legitimate guest access, isolated from the main corporate network, and administrators get full control and reports.
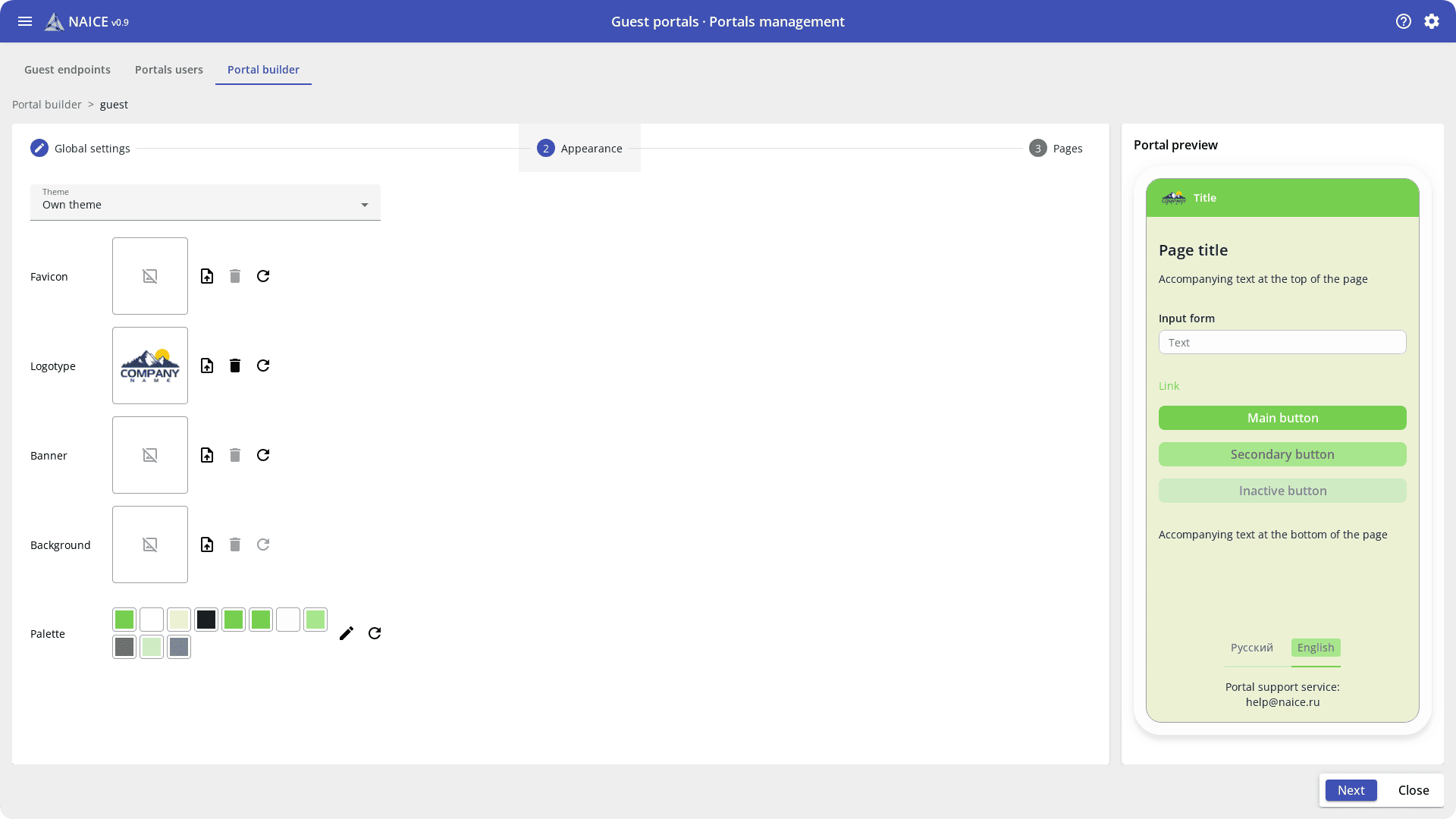
The built-in portal designer will help you customize the authorization page appearance to match the company’s corporate style, add a logo, change the colors, and personalize the greeting text.
Profiles and policies
Based on profiling, NAICE determines the device type by a variety of criteria, including MAC-OUI or DHCP probes, and automatically applies the appropriate access policy and group to it. This allows the system to understand what exactly has connected to the network: a workstation, a phone, a router, etc.
Policies set the "rules of the game" that determine the behavior of the system when requesting access for each device and user. NAICE includes RADIUS, TACACS+, and profiling policies. The administrator configures them once, and NAICE automatically recognizes new devices and applies the specified policies to them: allocates the necessary VLANs, sets filtering rules (ACL), and provides access according to the specified terms.
High availability
The Network Access Control (NAC) system is a crucial element of the infrastructure. Its failure can paralyze the entire company operation. The NAICE architecture includes support for a 1+1 hot standby: if one of the clusters fails for any reason, the second one immediately takes over all traffic without interrupting the service. In the future, the system will support a 1+1 Active-Active redundancy with load balancing towards NAICE.
What's in development
NAICE is being developed taking into account user feedback and analysis of trends in network security. Nearest plans:
- Development of a role-based model for managing network administrator rights (RBAC). Instead of assigning specific permissions, roles with predefined sets of rights will be used.
- Integration with SIEM systems. This will ensure the transfer of security events to other systems for centralized analysis and correlation with data from other sources. This will allow you to identify complex attacks that affect multiple infrastructure components and effectively counter them.
- Logging user actions. Recording operations to ensure auditing and investigation of security incidents.
Plans for 2026:
- Authorization of NAICE administrators via MS AD/LDAP. This will simplify account management and provide a single point of authentication in the corporate environment.
- TLS encryption for interaction with MS AD. This will make the transmission of authentication data more secure.
- Dynamic change of access rights without reconnecting the device (Radius CoA). If a user violates security policies or their rights in the enterprise change, the restrictions will be applied immediately.
- Support for personal devices of employees for work tasks on the corporate network (BYOD). Separation of corporate and personal traffic, control of access to corporate data, and compliance with security policies.
How to test NAICE
The best way to understand whether NAICE is right for your infrastructure is to test the system. A free test will reveal how well the product fulfills your current needs, if there are any limitations, and how it fits into your IT infrastructure development plans. To learn more about NAICE testing and purchasing, please contact the Eltex Sales Department at foreign.sales@eltex-co.ru.