Unified network access control with NAICE system

Description
Every year, corporate networks face an increasing number of threats. Data leaks, attacks via compromised devices, and unauthorized access attempts have become a reality for companies of all sizes and in all industries. To effectively control connections, enterprises use specialized NAC (Network Access Control) systems. Without them, it is impossible to guarantee reliable protection, and for organizations working with sensitive information, it is impossible to ensure compliance with regulatory requirements.
With over 30 years of experience in developing telecommunications equipment, we have created our own NAICE system, which takes into account operational practices and customer requirements. It is used in corporate organizations, industrial enterprises, banking, telecommunications, and government sectors.
Solution Architecture
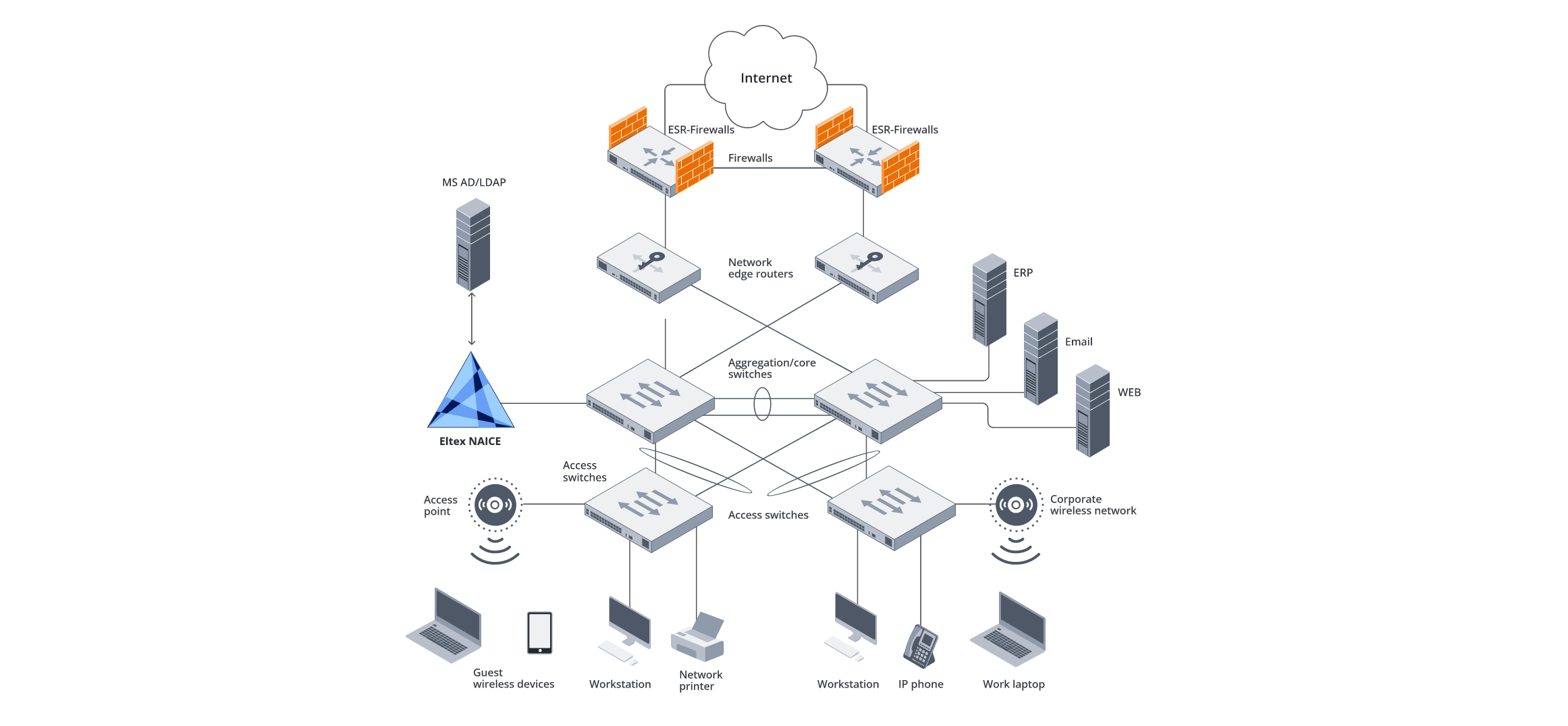
NAICE is a software that comprehensively covers the task of access management: from organizing user connections to Wi-Fi or Ethernet networks to controlling administrator rights.
The solution is compatible with equipment from Eltex and other manufacturers.
Network management and convenient web interface
Management is carried out through a convenient and intuitive web interface. Basic configuration includes adding network devices and profiles, connecting identification sources, creating identification chains and authorization profiles, and developing access policies.
User authentication and authorization via the RADIUS protocol
The architecture is based on the RADIUS client-server protocol (802.1x standard) with support for EAP-PEAP, PAP, MSCHAPv2, and EAP-TLS. It provides a complete cycle of authentication, authorization, and accounting (AAA) for user actions.
For devices that do not support 802.1X, MAC Authentication Bypass (MAB) based on MAC addresses is provided.
NAICE integrates with internal databases and external identification sources such as Microsoft Active Directory and OpenLDAP, allowing you to use existing corporate account databases without having to duplicate them. Access policies are automatically applied when a client's status changes. For example, when an employee is dismissed or removed from the database, the access to network resources is automatically denied.
Administrator authentication and authorization via the TACACS+ protocol
The system also supports the TACACS+ protocol, designed for centralized administrator authentication, control of their access rights, and logging of actions performed. Its key advantage is centralized authentication and authorization, which provide flexible access rights management. Administrators can create privilege profiles and rules tailored to specific business tasks using both precise commands and regular expression-based templates, which is relevant for large infrastructures with a large number of devices.
The protocol provides capabilities for detailed auditing of all interactions with network equipment. All administrator actions are logged and, if necessary, notifications about them are sent in syslog format to a third-party server. Thus, if an engineer changes the settings of a router, switch, or other equipment, the system records which command was entered, by whom, and at what time. This helps to quickly restore the chronology of actions and identify the problem when it arises.
Captive portal
NAICE provides a Captive Portal service for temporary wireless connections for users and guests. The guest portal provides secure connections for third-party devices and helps to restrict their access to isolated network segments.
New clients are authorized via SMS, through an internal database, or using external directories. When SMS authorization is selected, integration with any SMS gateways is provided for sending one-time codes. Administrators can set the duration of a guest account for re-authorization. Using the integrated web page builder, the portal can be designed in accordance with the company's corporate identity.
This mechanism is convenient in large infrastructures with high visitor traffic, such as airports. Passengers get access to Wi-Fi via SMS, the account is valid only for the duration of their stay in the network coverage area, and all corporate and service segments remain completely isolated. This provides convenience for thousands of users every day without compromising the security of internal resources.
System fault tolerance
Since NAICE is a critical element of the infrastructure, special attention is paid to fault tolerance. The system supports Active-Active (1+1) mode: if one server fails, the second instantly takes over its functions.
General solution scheme
Equipment